When talking about cloud computing, Information Security is a topic that always comes up, and that prompts us to think about the best ways to keep data confidential, intact and available.
A very common question would be how to access virtual machines on Azure, the famous RDP ( Remote Desktop Protocol ). Some practices to improve security are known, such as changing the default Remote Desktop connection port (3389), filtering source IPs that are allowed to connect, using certificates, among others.
As much care and precautions are taken, exposing RDP/SSH ports directly over the Internet is not a good practice and, in many cases, becomes a major vulnerability, which can be significantly exploited, threatening the availability of the resource and in some cases business continuity.
However, to mitigate this issue, there is a fully managed PaaS service that provides secure and continuous RDP and SSH access to the VMs, being accessed directly through the Azure portal, that is, you can connect to a VM, using an Internet browser! This service is called Azure Bastion.
Azure Bastion is provisioned directly on the VNet (virtual network), thus providing connectivity through RDP or SSH to VMs that are on this same network, that is, for this secure connection, the VM doesn’t need to have a public IP address or agent, not even special additional software installed.
Below is an architectural example of an Azure Bastion implementation :
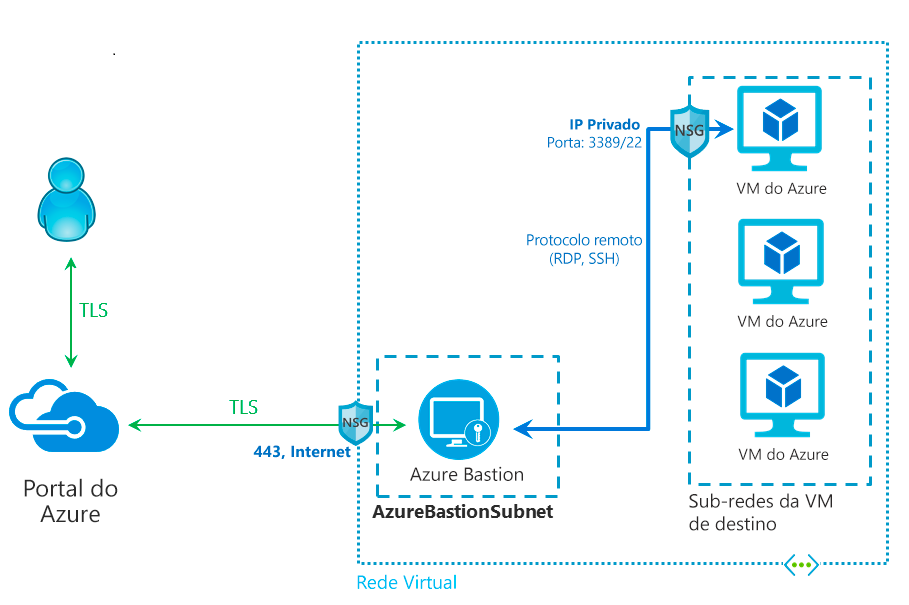
Below, we will walk through the implementation of this architecture, considering that there is already a VM connected to a specific VNet .:
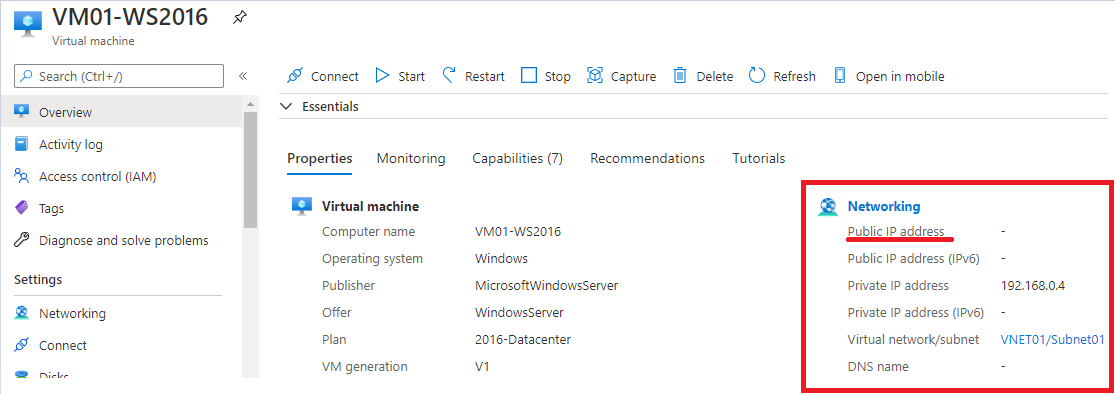
In this scenario, we will use the VM: VM01-WS2016, where below we see that there is no public IP assigned to it:
So, let’s follow the steps below to implement Azure Bastion :
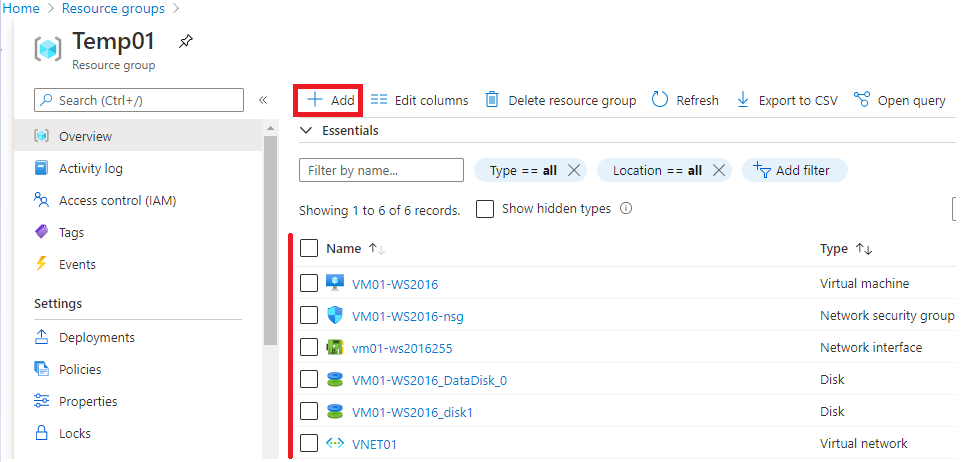
1 – Inside the Resource Group which the VNet associated with the VMs you want to have access to is located, click on “ +Add ”.
2 – On the next screen, in the search bar, type “ Bastion ” and select the option as soon as the result loads:

3 – On the next screen, click on “ Create ”:

4 – Now, let’s configure the Bastion settings. To do this, confirm the Subscription and Resource Group where Bastion will be deployed, along with its name and region:
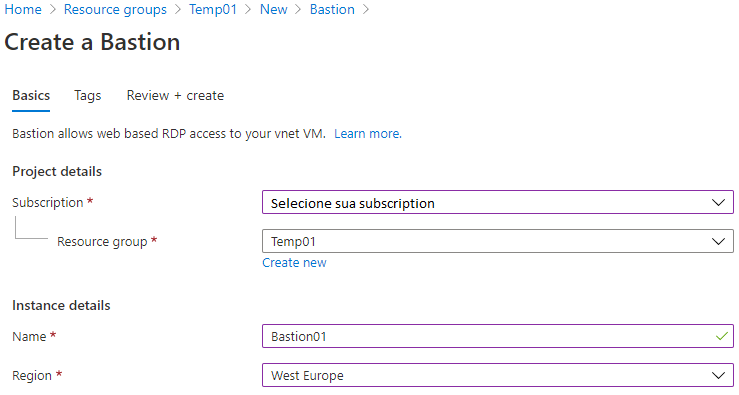
On this same screen, we will select the VNet to which the Bastion will be associated. Here, we have an important detail, where we must create a specific subnet for it, and the name must be “ AzureBastionSubnet ”. This subnet must be at least /27 as requested.:
So, click on “ Manage subnet configuration ” to create that subnet.
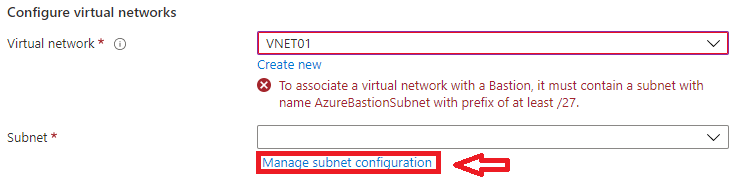
5- In this step, click on “ + Subnet ” to add the new subnet within the previously chosen VNet :
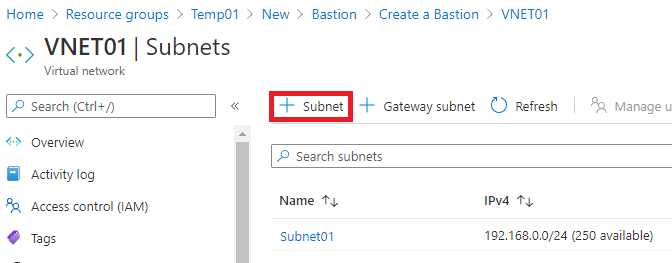
In the opened menu, name the new subnet as “ AzureBastionSubnet ” and configure the address range according to your VNet, remembering that a subnet of minimum size /27 is required. Then click on “ Save ”.
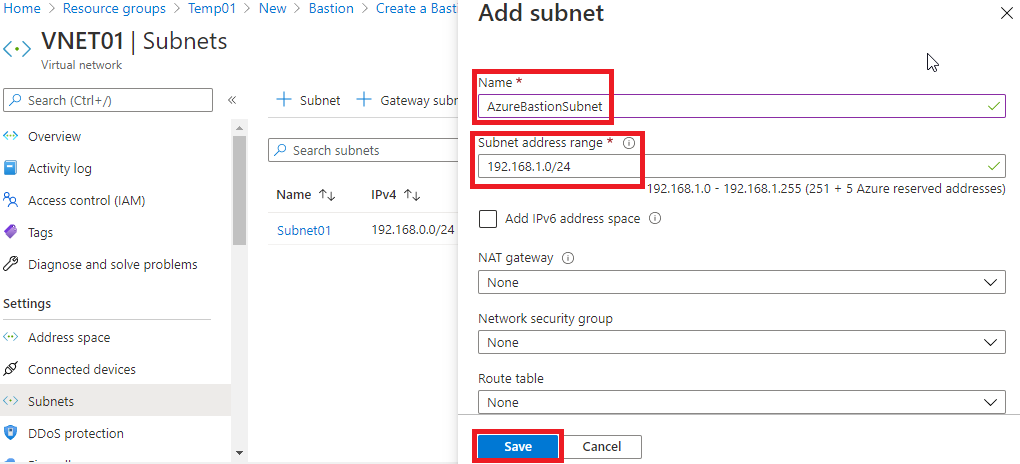
In this example, we now have two subnets,
- Subnet01, where is located the VM that we will access through Bastion and
- AzureBastionSubnet, which will be used by the Bastion service.
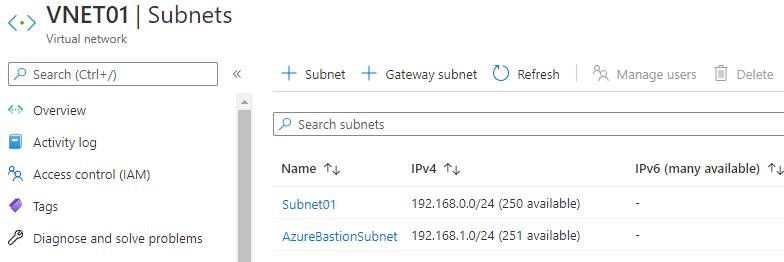
Returning to the previous screen in the Bastion creation, the subnet we created is now available and we must select it:
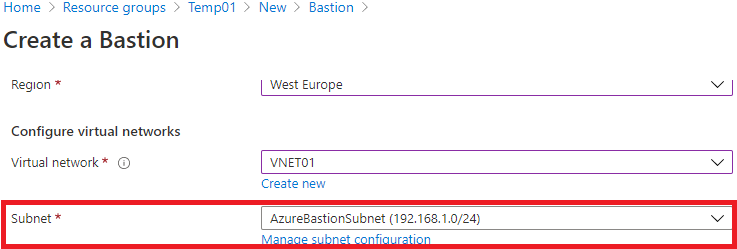
6 – Finally, we must assign a Public IP address to the Bastion service. If you don’t have any available, leave the “ Create New” option checked and name it. In the end, after completing all the settings, click on “ Next: Tags > ”.
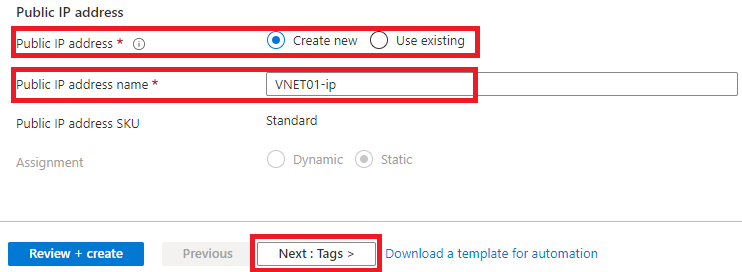
7 – Add TAGs according to your environment needs or compliance and at the end click on “ Review + Create ”.
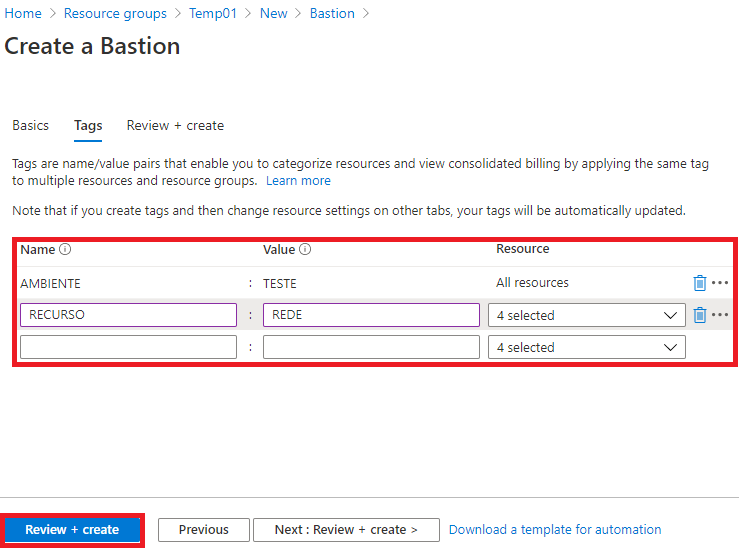
8 – On the next screen, wait for the validation step to be completed, review the data and click on “ Create ”:
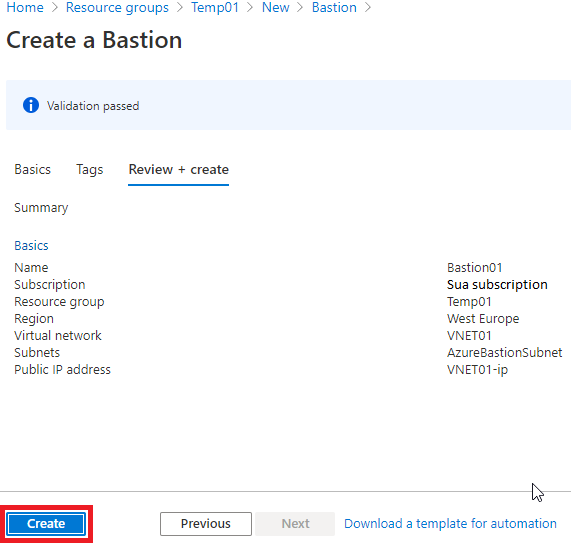
9 – You will be redirected to the next screen, where you must wait for the resource to be provisioned. Once completed, a similar screen will appear. Click on “ Go to the Resource ”
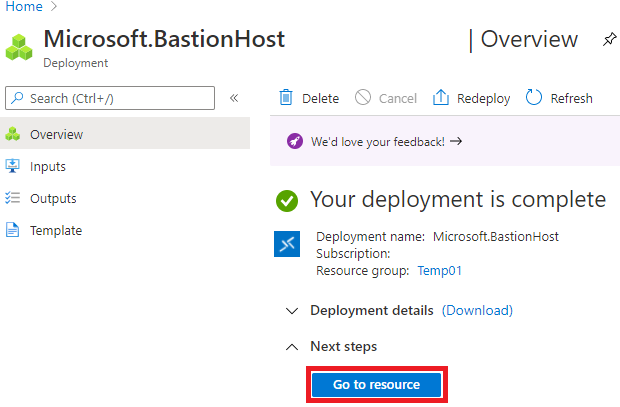
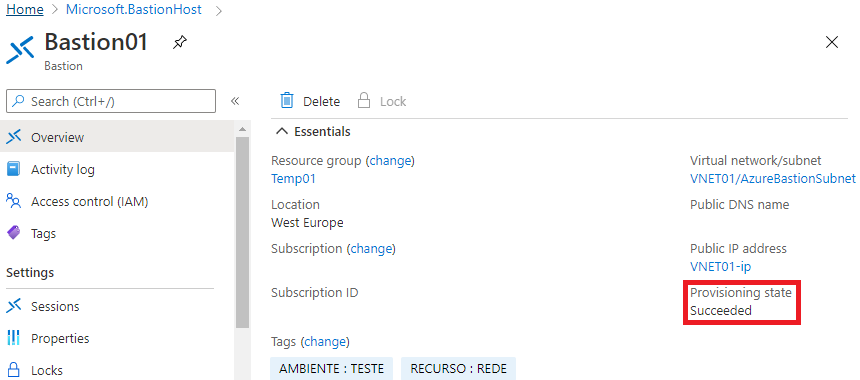
10 – On the screen of the Bastion resource that has been provisioned, observe if the provisioning status is as “ Succeeded ”. If so, then we will connect to the VM.
11 – Now, let’s go to the VM we want to connect (VM01-WS2016). Notice that it doesn’t have any Public IP assigned. So, click on the “Connect” option, then select “ Bastion ”.
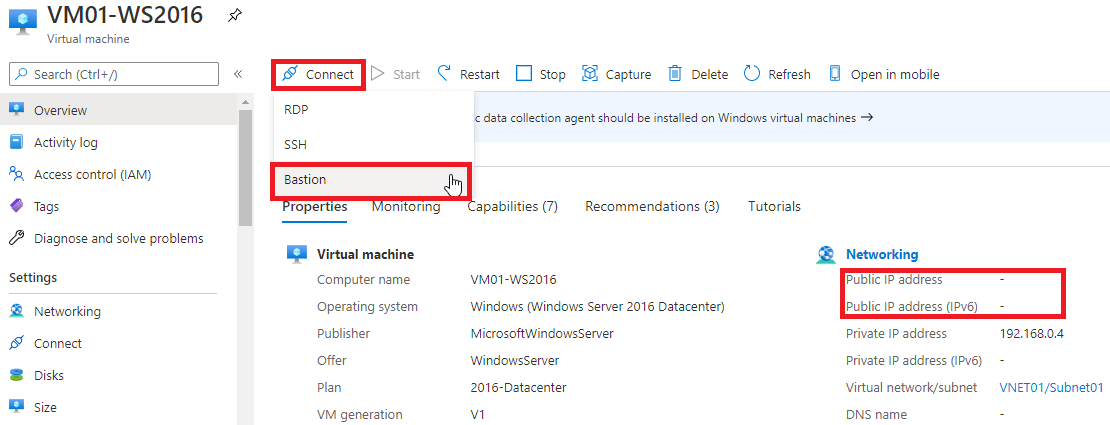
You will be directed to this screen, where you must click on “Use Bastion ” :
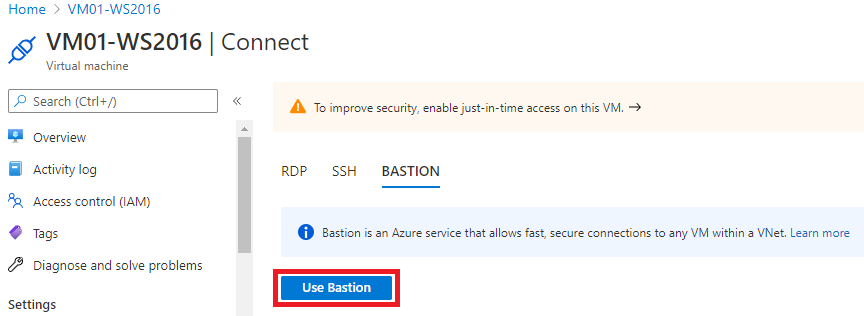
On the connection screen through Bastion, you must add the VM access credentials and click on “Connect”:
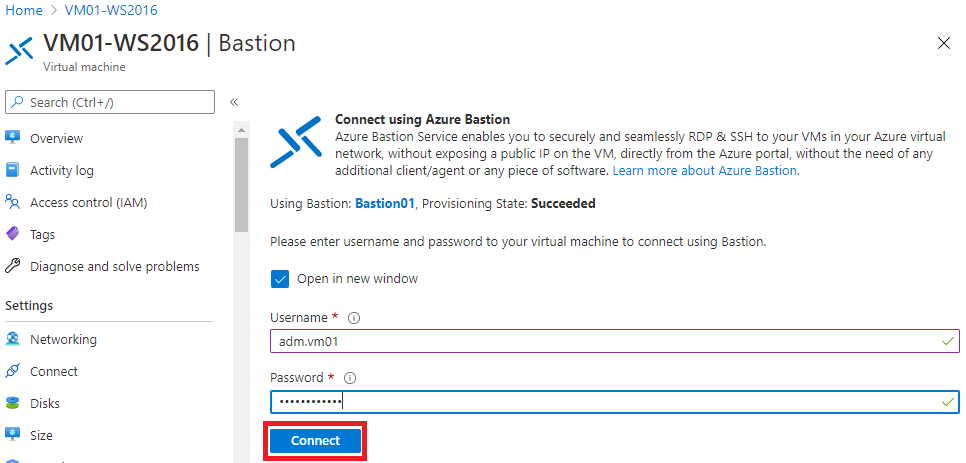
Then, a new tab will open with access to the management of the VM, directly through the browser. See below:
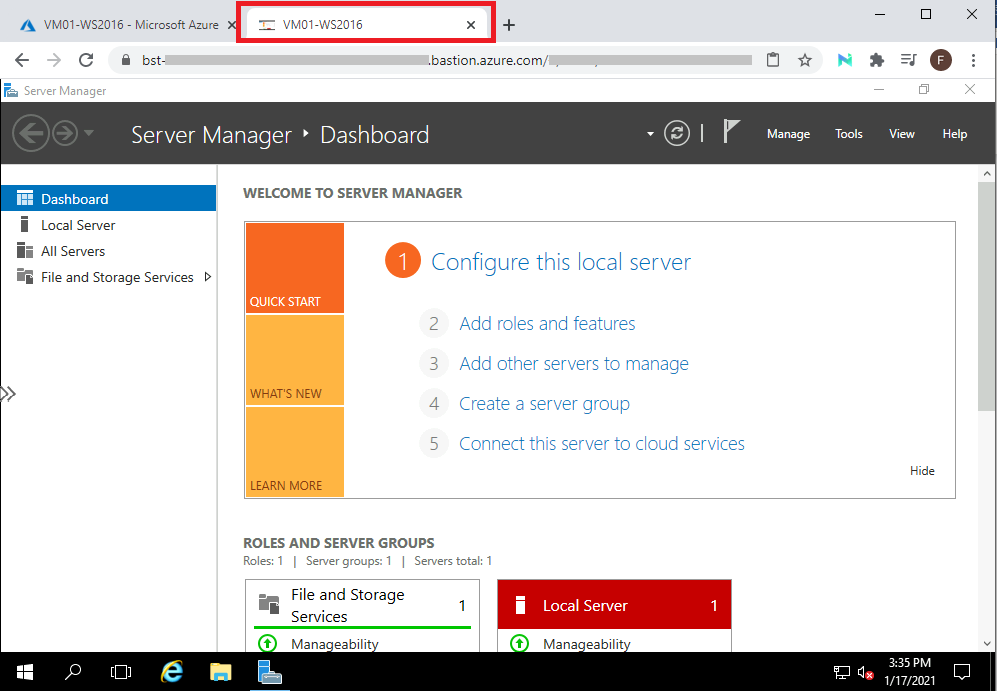
So, we concluded the Bastion service configuration and test, where it was possible to securely connect to a virtual machine without having to publish it directly on the internet through a Public IP. This is an important service that must be considered when there is a need to access the management of virtual machines.
For more detailed information about this service, such as pricing and frequently asked questions, such as if an Access CAL is required, which regions are available, among others, you can directly check the Microsoft documentation, using the links available below.
Sources for this article:
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
https://azure.microsoft.com/en-us/pricing/details/azure-bastion/
Thank you.
This blog is definitely rather handy since I’m at the moment creating an internet floral website – although I am only starting out therefore it’s really fairly small, nothing like this site. Can link to a few of the posts here as they are quite. Thanks much. Zoey Olsen